[IEEE COMST Survey] The Evolution of Quantum Secure Direct Communication: On the Road to the Qinternet
2024/03/26
Quantum information technology exploits the principles of quantum mechanics to acquire, process, and transmit information. Its main advantage is that it is capable of detecting if an eavesdropper is attempting to gain access to the confidential information transmitted. In addition to supporting ultimately secure communication, it is also capable of solving specific computational and search problems more efficiently than classical-domain computing, including breaking classical cyphering problems. Hence quantum computing poses a significant threat to the security of traditional asymmetric cryptographic systems based on high-complexity classical mathematical problems, such as the factorization of large numbers. Quantum communication is capable of resisting quantum computing attacks and achieve "post-quantum" security of communication. Quantum secure direct communication (QSDC) leverages quantum states for securely transmitting information over a noisy and potentially wiretapped channel, as a benefit of its eavesdropping detection capability. It has been proven to be information-theoretically secure and has transitioned from theory to experimentation, gradually migrating into the realm of practical applications.
In this context, the paper entitled “The Evolution of Quantum Secure Direct Communication: On the Road to the Qinternet” by Dong Pan, Gui-Lu Long, Liuguo Yin, Yu-Bo Sheng, Dong Ruan, Soon Xin Ng, Jianhua Lu, and Lajos Hanzo, presents a comprehensive survey. Dong Pan and Gui-Lu Long are from the Quantum Secure Direct Communication Group, Beijing Academy of Quantum information Sciences. It describes the principles and research progress of QSDC. Briefly, the family of quantum communication protocols includes quantum key distribution (QKD), quantum teleportation (QT), quantum secret sharing (QSS), and QSDC as shown in Figure 1 in chronological order. The paper commences by discussing the impact of quantum computing on classical cryptographic systems. As shown in Figure 2, it compares classical secure communication, quantum key distribution, and QSDC from the perspective of communication models. The paper then outlines the significant milestones in the evolution of QSDC. To garner broad interest, it presents the fundamental principles involved in quantum communication, including both its theoretical aspects and experimental techniques. The authors provide a detailed overview of the typical protocols conceived for QSDC, along with advances in its security analysis and expanded applications in cryptographic protocol design. The paper also introduces multi-user networking schemes designed for QSDC. Then, the recent experimental progress of QSDC is presented in. Finally, the paper summarizes a whole suite of open challenges and outlines a range of promising future research directions.
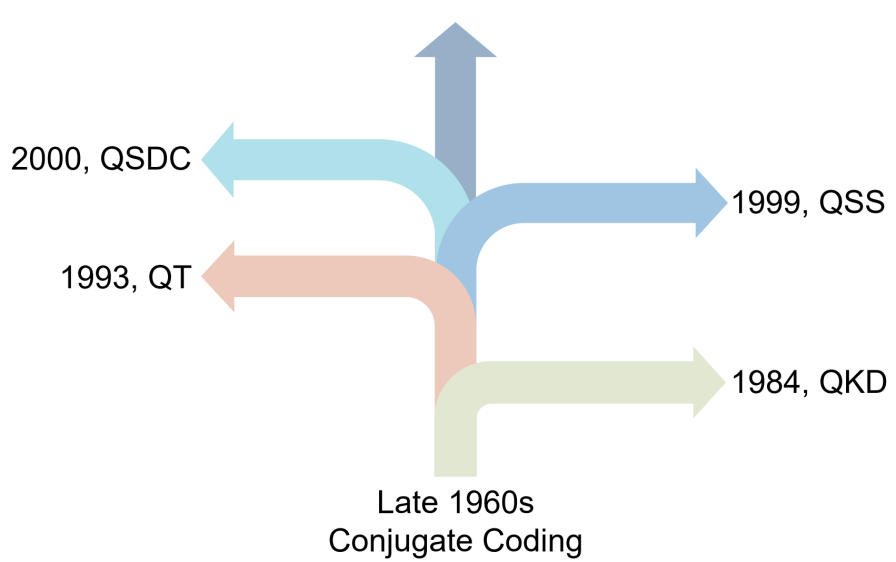
Figure 1. The main branches of quantum communication. QKD, quantum key distribution; QT, quantum teleportation; QSS, quantum secret sharing; QSDC, quantum secure direct communication.
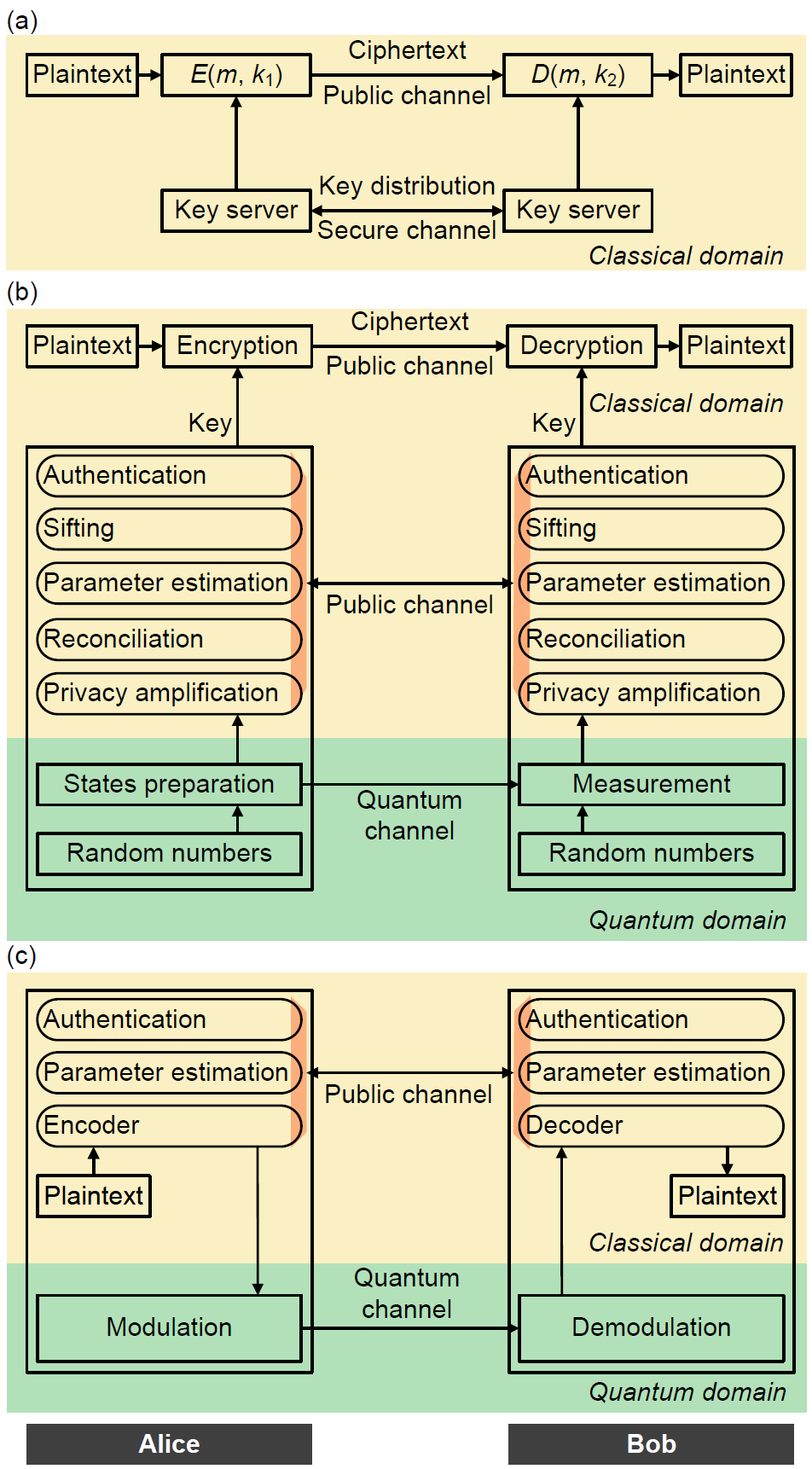
Figure 2. Different models of communication systems. (a) classical cryptosystem. (b) QKD system. Key agreement is carried out by QKD, and information is transmitted via classical communication, the same as in (a). (c) QSDC system. No key distribution, no key management and no ciphertext are required in QSDC.
 中文
中文 Email
Email QCloud
QCloud Log in
Log in
